Happening
How to Identify and Remove VPN Apps That Contain 911 S5 Backdoors

The FBI, the Defense Criminal Investigative Service, and the Department of Commerce’s Office of Export Enforcement have published a public service announcement (the “PSA”) for individuals and businesses to better understand and guard against the 911 S5 residential proxy service and botnet. The PSA is available at ic3.gov/Media/Y2024/PSA240529.
As explained in the PSA, 911 S5 began operating in May 2014 and was taken offline by the administrator in July 2022 before reconstituting as Cloudrouter in October 2023. 911 S5 was likely the largest residential proxy service and botnet with over 19 million compromised IP addresses in over 190 countries and confirmed victim losses in the billions of dollars.
Free, illegitimate VPN applications that were created to connect to the 911 S5 service are: MaskVPN, DewVPN, PaladinVPN, ProxyGate, ShieldVPN, and ShineVPN.
Unaware of the proxy backdoor, once users downloaded these VPN applications, they unknowingly became a victim of the 911 S5 botnet. The proxy backdoor enabled 911 S5 users to re-route their devices through victims’ devices, allowing criminals to carry out crimes such as bomb threats, financial fraud, identity theft, child exploitation, and initial access brokering. By using a proxy backdoor, criminals made nefarious activity appear as though it was coming from the victims’ devices.
The below information is intended to help identify and remove 911 S5’s VPN applications from devices or machines.
Before electing to use this information, users may want to consult with legal counsel and cybersecurity professionals, potentially including an incident response firm if they deem necessary, to explore all options and assist with any remediation efforts to avoid further harm by malicious software applications or botnets. The FBI makes no warranties or representations regarding the efficacy of this information.
Check for Running Services
1. Press Control+Alt+Delete on the keyboard and select the “Task Manager” option or right-click on the Start menu (Windows icon) and select the “Task Manager” option.
2. Task Manager should now be running. Under the “Process” tab, look for the following:
- MaskVPN (mask_svc.exe)
- DewVPN (dew_svc.exe)
- PaladinVPN (pldsvc.exe)
- ProxyGate (proxygate.exe, cloud.exe)
- ShieldVPN (shieldsvc.exe)
- ShineVPN (shsvc.exe)
Example of running processes for ShieldVPN and ShieldVPN Svc:
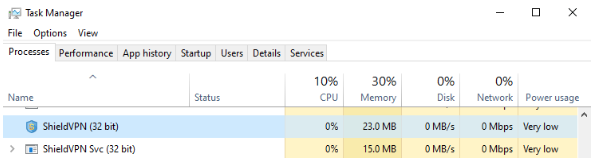
If Task Manager doesn’t detect any of these services, verify that by searching the Start menu for any traces of software labeled as “MaskVPN,” “DewVPN,” “ShieldVPN,” “PaladinVPN,” “ProxyGate,” or “ShineVPN.”
3. Click on the “Start” (Windows Icon) button typically found in the lower lefthand corner of the screen. Then, search for the following terms, which are the identified names of the malicious software applications:
- MaskVPN
- DewVPN
- ShieldVPN
- PaladinVPN
- ShineVPN
- ProxyGate
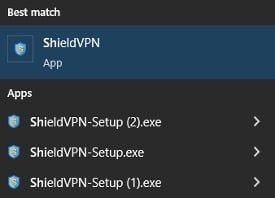
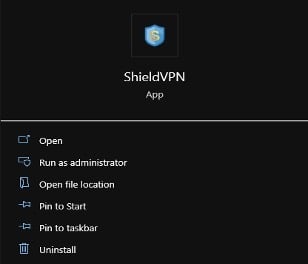
4. If one of the VPN applications is found, an uninstaller is sometimes located under the Start menu option of the VPN application. The example image below shows an instance where the uninstall option isn’t available.
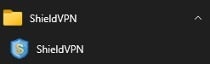
5. If the application doesn’t contain an uninstall option, then follow the steps below to attempt to uninstall the application:
- Click on the Start menu (Windows button) and type “Add or remove programs” to bring up the “Add and Remove Programs” menu.

- Search for the malicious software application names.
An example image below shows the ShieldVPN application found within the “Add or remove programs” application list. Once you find the application in the list, click on the application name and select the “Uninstall” option.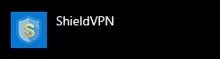
- After the application is uninstalled, you can try to verify that the application has been removed by clicking on “Start” (Windows Icon) and typing “File Explorer.”
- Click on the drive letter “C:”—sometimes labeled as “Windows (C:)”—and navigate to “Program Files(x86).” Then, look for the malicious software application names in the list of files and folders.
![Click on the drive letter aC:a (Sometimes labeled as aWindows (C:)a) and navigate to Program Files(x86) and look for the malicious software application names in the list of files and folders.
For ProxyGate, navigate to C:\users\[Userprofile]\AppData\Roaming\ProxyGate.
If you do not see any folder labeled MaskVPN, DewVPN, ShineVPN, ShieldVPN, PaladinVPN, or Proxyate, then this particular malicious software application may not be installed.](https://www.fbi.gov/image-repository/911s5-shield-directory-022924.jpg/@@images/9f484d42-50ed-4148-9d5a-0993779d8c25.jpeg)
- For ProxyGate, navigate to “C:\users\[Userprofile]\AppData\Roaming\ProxyGate.”
- If you don’t see any folder labeled “MaskVPN,” “DewVPN,” “ShineVPN,” “ShieldVPN,” “PaladinVPN,” or “Proxygate,”
then this particular malicious software application may not be installed. - If a service was found running, but not found under the Start menu or “Add and Remove Programs,” then:
- Navigate to the directories described in directions 5d and 5e.
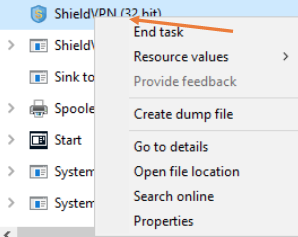
- Open “Task Manager.”
- Select the service related to one of the identified malicious software applications running in the process tab.
- Select the option “End task” to attempt to stop the process from running.
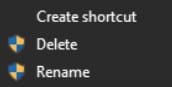
- Right-click on the folder named “MaskVPN,” “DewVPN,” “ShineVPN,” “ShieldVPN,” “PaladinVPN,” or “ProxyGate.”
- Select the “Delete” option.
- You can also select all files found within the folder and then select the “Delete” option.
- If you try to delete the folder—or to delete all files located inside the folder—and receive an error message, be sure that you’ve ended all processes related to the malicious software within in Windows Task Manager, as described in step 5g.
6. Based on the instructions found above, were you able to locate any of the listed files on your computer? Please click this link to select “Yes” or “No.” No other information is needed.

Happening
Telegram CEO on Legal Challenges in France

❤️ Thanks everyone for your support and love!
Last month I got interviewed by police for 4 days after arriving in Paris. I was told I may be personally responsible for other people’s illegal use of Telegram, because the French authorities didn’t receive responses from Telegram.
This was surprising for several reasons:
- Telegram has an official representative in the EU that accepts and replies to EU requests. Its email address has been publicly available for anyone in the EU who googles “Telegram EU address for law enforcement”.
- The French authorities had numerous ways to reach me to request assistance. As a French citizen, I was a frequent guest at the French consulate in Dubai. A while ago, when asked, I personally helped them establish a hotline with Telegram to deal with the threat of terrorism in France.
- If a country is unhappy with an internet service, the established practice is to start a legal action against the service itself. Using laws from the pre-smartphone era to charge a CEO with crimes committed by third parties on the platform he manages is a misguided approach. Building technology is hard enough as it is. No innovator will ever build new tools if they know they can be personally held responsible for potential abuse of those tools.
Establishing the right balance between privacy and security is not easy. You have to reconcile privacy laws with law enforcement requirements, and local laws with EU laws. You have to take into account technological limitations. As a platform, you want your processes to be consistent globally, while also ensuring they are not abused in countries with weak rule of law. We’ve been committed to engaging with regulators to find the right balance. Yes, we stand by our principles: our experience is shaped by our mission to protect our users in authoritarian regimes. But we’ve always been open to dialogue.
Sometimes we can’t agree with a country’s regulator on the right balance between privacy and security. In those cases, we are ready to leave that country. We’ve done it many times. When Russia demanded we hand over “encryption keys” to enable surveillance, we refused — and Telegram got banned in Russia. When Iran demanded we block channels of peaceful protesters, we refused — and Telegram got banned in Iran. We are prepared to leave markets that aren’t compatible with our principles, because we are not doing this for money. We are driven by the intention to bring good and defend the basic rights of people, particularly in places where these rights are violated.
All of that does not mean Telegram is perfect. Even the fact that authorities could be confused by where to send requests is something that we should improve. But the claims in some media that Telegram is some sort of anarchic paradise are absolutely untrue. We take down millions of harmful posts and channels every day. We publish daily transparency reports (like this or this ). We have direct hotlines with NGOs to process urgent moderation requests faster.
However, we hear voices saying that it’s not enough. Telegram’s abrupt increase in user count to 950M caused growing pains that made it easier for criminals to abuse our platform. That’s why I made it my personal goal to ensure we significantly improve things in this regard. We’ve already started that process internally, and I will share more details on our progress with you very soon.
I hope that the events of August will result in making Telegram — and the social networking industry as a whole — safer and stronger. Thanks again for your love and memes 🙏. Credit source Pavel Durov via Telegram.
Happening
What is crowd strike and why is everyone talking about it today

CrowdStrike is a cybersecurity company, kind of like a digital knight in shining armor for businesses. They protect companies from cyberattacks and online threats.
Today, there’s a buzz around CrowdStrike because they’re dealing with a bit of a hiccup. One of their updates for Windows computers malfunctioned, causing some systems to act wonky. It’s important to note, however, that this wasn’t a cyberattack, more of a friendly fire situation. CrowdStrike is assuring everyone they’ve identified the problem, fixed it, and are patching things up as we speak.
Here’s a story for you:
It was a tense morning at DigiCorp, a tech startup. Alarms blared on laptops, throwing up error messages. Sarah, the head of IT, was fielding frantic calls from colleagues. Their data, their entire business, seemed to be on the fritz.
“Is it a ransomware attack?” someone shouted.
Sarah took a deep breath. “Let’s not panic. It could be anything. First, let’s isolate the problem and see if CrowdStrike can shed some light.”
Moments later, Sarah sighed with relief. CrowdStrike confirmed it wasn’t a malicious attack, but a glitch with their own update. A wave of laughter rippled through the stressed-out team.
“Well, that’s a relief,” Matt, a programmer, chuckled. “Though, maybe CrowdStrike needs to polish their knightly armor a bit.”
By lunchtime, CrowdStrike had rolled out a fix, and DigiCorp was back in business. Sarah sent a quick thank you note to their cybersecurity partners. Though it was a scare, it was a good reminder of how important CrowdStrike was in keeping their digital world safe.
Happening
What are the disadvantages of YouTube monetization?
YouTube has become a popular platform for content creators to share their work and potentially earn money. However, while monetization offers exciting opportunities, it also comes with its fair share of monetization challenges. In this article, we’ll explore the potential drawbacks of YouTube monetization and how they can impact creators.
Table of Contents
Understanding YouTube Monetization Challenges
Before diving into the disadvantages, it’s essential to understand that YouTube monetization isn’t always a straightforward path to success. Many creators face various hurdles and obstacles that can affect their ability to earn revenue consistently.
The Pressure to Produce Consistently
One of the primary monetization challenges creators face is the constant pressure to produce content. To maintain a steady income, YouTubers often feel compelled to:
- Upload videos frequently
- Keep up with trends
- Constantly engage with their audience
This pressure can lead to burnout and may compromise the quality of content over time.
Dealing with Algorithm Changes
YouTube’s algorithm plays a crucial role in content discovery and monetization. However, frequent changes to this algorithm can present significant monetization challenges:
- Videos may suddenly receive less exposure
- Ad revenue can fluctuate unpredictably
- Creators may need to adapt their content strategy frequently
Monetization Challenges: Advertiser-Friendly Content
To monetize videos effectively, creators must adhere to YouTube’s advertiser-friendly guidelines. This requirement can lead to several issues:
- Self-censorship
- Limited creative freedom
- Difficulty covering certain topics or niches
Some creators find these restrictions stifling and struggle to balance their artistic vision with monetization requirements.
The Unpredictability of Ad Revenue
Ad revenue, a primary source of income for many YouTubers, can be highly unpredictable. This volatility presents ongoing monetization challenges, including:
- Seasonal fluctuations in ad rates
- Changes in advertiser spending
- Impact of global events on ad budgets
These factors can make it difficult for creators to plan their finances and rely on YouTube as a stable income source.
Copyright Issues and Demonetization
Navigating copyright laws on YouTube can be tricky. Creators face monetization challenges when:
- Using copyrighted music or footage
- Dealing with false copyright claims
- Risking demonetization due to copyright strikes
These issues can result in loss of revenue and potentially affect a channel’s standing on the platform.
Competition and Market Saturation
As more people turn to YouTube for income, the platform becomes increasingly competitive. This saturation leads to monetization challenges such as:
- Difficulty standing out in a crowded market
- Lower ad rates due to increased supply of content
- Pressure to create clickbait or sensational content
Creators may find it harder to grow their audience and maintain sustainable revenue streams in this environment.
Privacy and Personal Life Impacts
Successful YouTube monetization often requires creators to share aspects of their personal lives, which can lead to:
- Loss of privacy
- Online harassment or stalking
- Difficulty separating work from personal life
These factors can take a toll on a creator’s mental health and overall well-being.
Dependence on a Single Platform
Relying solely on YouTube for income can be risky. Monetization challenges arise when:
- YouTube changes its policies
- Technical issues affect the platform
- A creator’s account faces suspension or termination
Diversifying income sources becomes crucial to mitigate these risks.
Conclusion
While YouTube monetization offers exciting opportunities for content creators, it’s important to be aware of the potential drawbacks. From algorithm changes to privacy concerns, these monetization challenges can significantly impact a creator’s journey on the platform.
By understanding these challenges, aspiring YouTubers can better prepare themselves for the realities of content creation as a career. It’s crucial to approach YouTube monetization with a balanced perspective, weighing the potential rewards against the possible disadvantages.
Ultimately, success on YouTube requires not just great content, but also the ability to navigate these monetization challenges effectively. With the right strategy and mindset, creators can work towards building a sustainable and rewarding presence on the platform.
-
SEO3 months ago
How to Increase Conversion Rate in 2024: 15 Effective Strategies
-
SEO3 months ago
What is SEO and how it works
-
GamersX3 months ago
Call of Duty: Black Ops 6 Officially Announced, Full Reveal on June 9
-
SEO3 months ago
Is Google Keyword Planner worth it?
-
SEO3 months ago
Tips for Successful SEO Optimization for Personal Trainers
-
WordPress3 months ago
Constant Updates and Support for WordPress
-
WordPress3 months ago
GeneratePress 3
-
Technical Writing3 months ago
Building Quality Backlinks for Improved SEO














